Sub-pipeline example: Pipeline with build secrets
Source code for this example.
-
In the Radix application repository create a folder
tekton. This folder need to be in the configuration branch and in the same folder, whereradixconfig.yamlfile is located (by default it is a root of the repository). -
The sub-pipeline in this example runs one task.
-
Create a file
use-secrets-task.yamlfor the taskuse-secrets. This task has one step "show-secrets", which runs in the container with Alpine Linux.- The step runs a script with one commands, showing secrets, mapped to step's container environment variables and files.
- The task step has description of environment variable
DB_SERVER_NAMEin the fieldenv, which will be created in the step's container. These environment variable gets value from the secretDB_SERVER, referencing to them viasecretKeyRefwith$(radix.build-secrets)and a secret name:
env:
- name: DB_SERVER_NAME
valueFrom:
secretKeyRef:
name: $(radix.build-secrets)
key: DB_SERVER- The task step also has description of mapping from the build secret and environment variables in the field
envFrom, which will create in the step's container environment variables for each secret entry in the build secret. These environment variables can get optional prefix to their names, specified in the fieldprefix(e.g.BUILD_SECRET_in this example, so for the secretDB_SERVERthe environment variable will beBUILD_SECRET_DB_SERVER). Reference to the build secrets are defined with a fieldsecretRef.nameand with$(radix.build-secrets)as a secret name:
envFrom:
- secretRef:
name: $(radix.build-secrets)
prefix: BUILD_SECRET_-
The task
specalso contains a fieldvolumes. In this example volumes are mapped to build secrets with particular secret entries, split to two volumes and separateitemsin volumes. Build secrets are referred as$(radix.build-secrets)in a fieldsecret.secretNameof each of volumes.- Volume
volume-with-passwordmaps the build secretDB_PASSWORDto a filepassword.txt - Volume
volume-certmaps the build secretsCERT_PRIV_KEYandCERT_PUB_KEYto filespriv/cert.keyandpriv/cert.pubcorrespondingly. Folderprivin thepathwill be a sub-folder withing themountPathofvolumeMountsin task's steps:
volumes:
- name: volume-with-password #a volume, which can be shared between task steps
secret:
secretName: $(radix.build-secrets)
items:
- key: DB_PASSWORD
path: password.txt
- name: volume-cert
secret:
secretName: $(radix.build-secrets)
items:
- key: CERT_PRIV_KEY
path: priv/cert.key
- key: CERT_PUB_KEY
path: priv/cert.pub - Volume
File use-secrets-task.yaml
apiVersion: tekton.dev/v1
kind: Task
metadata:
name: use-secrets
spec:
steps:
- name: show-secrets
image: alpine
env:
- name: DB_SERVER_NAME
valueFrom:
secretKeyRef:
name: $(radix.build-secrets)
key: DB_SERVER
envFrom:
- secretRef:
name: $(radix.build-secrets)
prefix: BUILD_SECRET_
script: |
echo "--- Print environment variables, with names containing 'DB_'"
printenv | grep "DB_"
echo "--- Print folders: /var/*-volume"
ls /var/*-volume
echo "--- Print file: /var/pass-volume/password.txt"
cat /var/pass-volume/password.txt
echo "--- Print file: /var/cert-volume/priv/cert.key"
cat /var/cert-volume/priv/cert.key|head -n 3
echo "--- Print file: /var/cert-volume/priv/cert.pub"
cat /var/cert-volume/priv/cert.pub|head -n 3
:
volumeMounts:
- name: volume-with-password
mountPath: /var/pass-volume #mount this volume to a folder "/var/task-volume"
- name: volume-cert
mountPath: /var/cert-volume #mount this volume to a folder "/var/cert-volume"
volumes:
- name: volume-with-password #a volume, which can be shared between task steps
secret:
secretName: $(radix.build-secrets) #map Radix build secrets to a volume
items:
- key: DB_PASSWORD #map this secret to a file "password.txt"
path: password.txt
- name: volume-cert #a volume, which can be shared between task steps
secret:
secretName: $(radix.build-secrets) #map Radix build secrets to a volume
items:
- key: CERT_PRIV_KEY #map this secret to a file "priv/cert.key"
path: priv/cert.key
- key: CERT_PUB_KEY #map this secret to a file "priv/cert.pub"
path: priv/cert.pub
- Create a file
pipeline.yaml. Add a task in thetaskslist: give it a name (it can be any name, unique within this sub-pipeline), in the propertytaskRef("reference to a task") put the value from the propertymetadata.nameof the task, created above:
apiVersion: tekton.dev/v1
kind: Pipeline
metadata:
name: pipeline-example-with-secrets
spec:
tasks:
- name: use-secrets-for-db #name of the task "use-secrets" in this pipeline
taskRef:
name: use-secrets #task name
- File structure can be like this:
/
├── tekton/
│ ├── pipeline.yaml
│ └── use-secrets-task.yaml
└── radixconfig.yaml
- In the file
radixconfig.yamladd a fieldbuildwith sub-fieldsecrets, as described in theradixconfig.yamlreference. Values of these secrets will be passed to the sub-pipeline task with build secret reference$(radix.build-secrets):
spec:
build:
secrets:
- DB_SERVER
- DB_PASSWORD
- CERT_PRIV_KEY
- CERT_PUB_KEY
- DB_USER
- This sub-pipeline runs the task
use-secrets-for-db(which refers to the taskuse-secretsdescribed in the fileuse-secrets-task.yaml), which has one step, as described above. This step runs a script, which prints environment variables and files with values of mapped build secrets. Note:(column) - this is no-op shell command, added for more stable behaviour of the script (as explained in Sub-pipeline hints).
#!/usr/bin/env sh
echo "--- Print environment variables, with names containing 'DB_'"
printenv | grep "DB_"
echo "--- Print folders: /var/*-volume"
ls /var/*-volume
echo "--- Print file: /var/pass-volume/password.txt"
cat /var/pass-volume/password.txt
echo "--- Print file: /var/cert-volume/priv/cert.key"
cat /var/cert-volume/priv/cert.key|head -n 3
echo "--- Print file: /var/cert-volume/priv/cert.pub"
cat /var/cert-volume/priv/cert.pub|head -n 3
First line of the script is shebang. It is recommended to use for consistent script behaviour. It can refer to a default shell
shor to a specific shell, existing in the step's image distribution, likebashfor Ubuntu:#!/usr/bin/env bash
-
Commit changes in the repository. Look at the details of a started Radix pipeline job (if the Radix app is connected to the GitHub WebHook, otherwise - start a job manually).
-
If build secrets were just added - the build will fail. Navigate to the "Configuration" page of the Radix application, fill in secrets in the section "Build secrets". In the page "Pipeline jobs" create a new job.
-
Navigate to the Radix pipeline step "Run pipeline", when it is running or completed: the pipelines overview page shows a table with a list of sub-pipelines - in this example it is one sub-pipeline "pipeline-example-with-secrets", running for an environment "dev", and the sub-pipeline status.
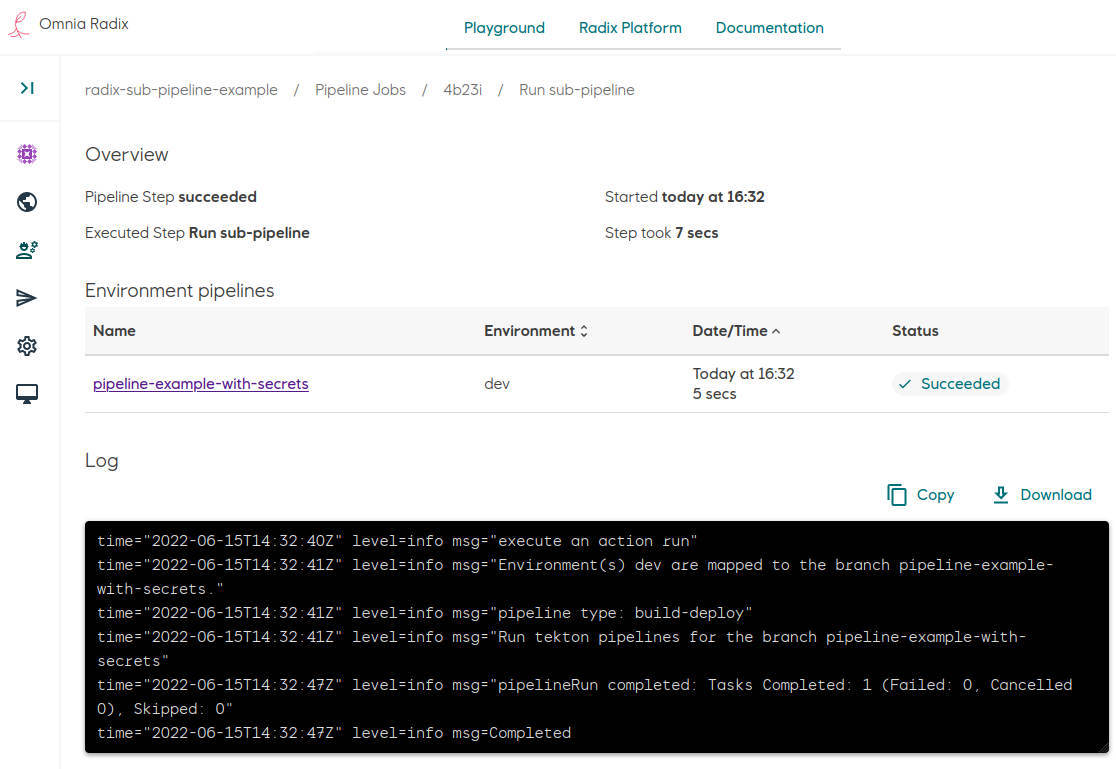
-
Navigate to the sub-pipeline (click on its name in the table row)
-
The sub-pipeline overview page shows a table with a list of this sub-pipeline's tasks - in this example it is one task "use-secrets-for-db", and the task status.
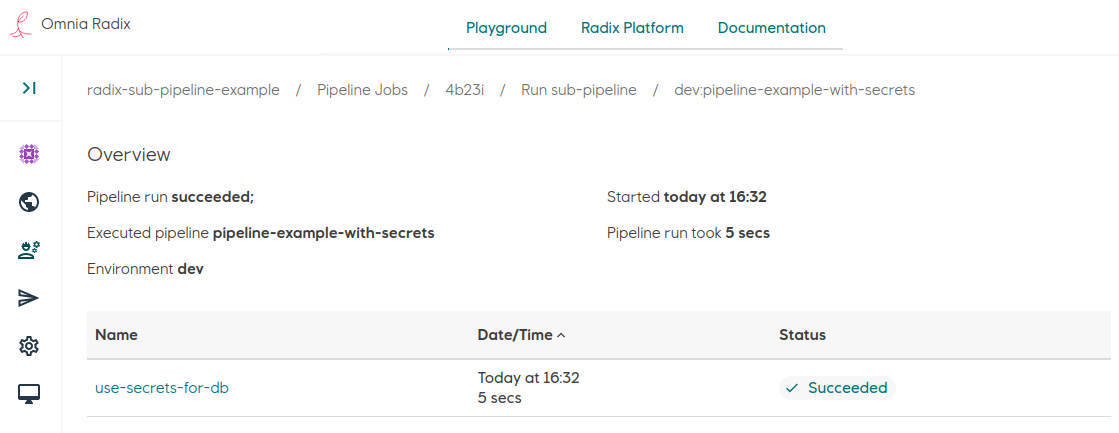
-
Navigate to the task (click on its name in the table row)
-
The sub-pipeline task overview page shows a table with a list of this task's steps - in this example it is one step "show-secrets", the step status and log.
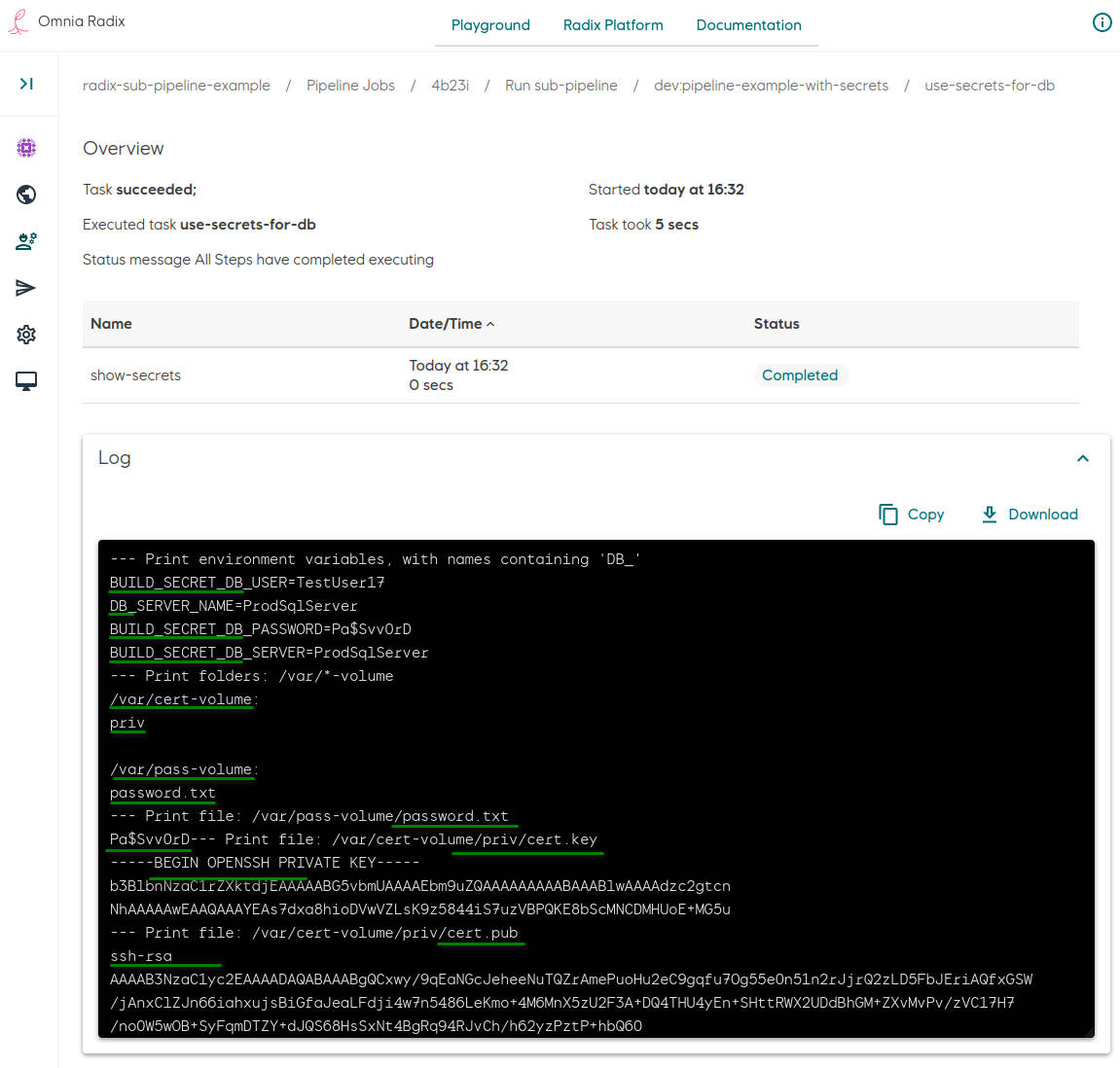
-
The log shows environment variables and file contents of the step container (output depends on the entered build secret contents):
--- Print environment variables, with names containing 'DB_'
BUILD_SECRET_DB_USER=TestUser17
DB_SERVER_NAME=ProdSqlServer
BUILD_SECRET_DB_PASSWORD=Pa$Svv0rD
BUILD_SECRET_DB_SERVER=ProdSqlServer
--- Print folders: /var/*-volume
/var/cert-volume:
priv
/var/pass-volume:
password.txt
--- Print file: /var/pass-volume/password.txt
Pa$Svv0rD--- Print file: /var/cert-volume/priv/cert.key
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAs7dxa8hioDVwVZLsK9z5844iS7uzVBPQKE8bScMNCDMHUoE+MG5u
--- Print file: /var/cert-volume/priv/cert.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCxwy/9qEaNGcJeheeNuTQZrAmePuoHu2eC9gqfu7Og55e0n51n2rJjrQ2zLD5FbJEriAQfxGSW/jAnxClZJn66iahxujsBiGfaJeaLFdji4w7n5486LeKmo+4M6MnX5zU2F3A+DQ4THU4yEn+SHttRWX2UDdBhGM+ZXvMvPv/zVC17H7/no0W5wOB+SyFqmDTZY+dJQS68HsSxNt4BgRq94RJvCh/h62yzPztP+hbQ60